Bridging The Gap: Marketing & Cybersecurity
Marketers are trained to treat security as IT’s responsibility. And IT departments don’t spend their waking hours worrying about marketing objectives.
But the reality is that high-stakes topics like cybersecurity touch both departments.
And while IT teams do spend their waking hours worrying about cyber threats, marketers don’t.
Between managing platforms and constantly juggling multiple priorities, marketers need to become more savvy when it comes to keeping customer data (and their own information) safe.
Here’s the reality:
- Wading into cyberspace without precautions is like a toddler facing the deep end without floaties.
- Digital marketing can feel like an undertow for marketers – uncharted waters (continuing the metaphor) where we dare not drift.
- But it’s actually an opportunity to shore up (we can’t stop! …we have a problem) security practices to the benefit of your customers and your own internal team.

Poor cybersecurity is a problem endemic to marketing. A blind spot for the industry. And here are a few ways to fix it.
Table of Contents
Remote Work, Compliance, and Cookies, Oh My!
On a good day, the cybersecurity landscape shifts as quickly as the tech that underlies it. But the work and marketplace changes of the last two years have thrust marketers and cybersecurity together in a REALLY uncomfortable way.
Combine these currents with the stern tightening of data practices like the General Data Protection Regulation (GDPR) in the EU and state legislation in California, New York, and Virginia, and you’ve got yourself the proverbial perfect storm.
In fact, the omnipresent risk of attacks and compliance failures are now one of the most significant risks businesses face.
Did you know board members can be held personally liable for breaches?
Gulp.
Yup. Oh, and by the way, your staff still needs to work (maybe some remotely), and you need to live up to marketing commitments like advertising, growing traffic, and nailing those conversion goals (to name a few).
You have to strike a balance between protecting your clients’ information and your networks and giving your team the trust and freedom to succeed and thrive.
No one wants to feel like they’re under constant surveillance or suspicion (Edward Snowden, anyone?).
We’ve faced it. We’ve wrestled with it. And while it’s an endless battle, we feel we’ve emerged stronger and prepared to face future threats. And we want you to feel that way, too.

But, we’re not IT experts, you say.
You don’t have to be.
Sound cybersecurity postures can be both a differentiator and a way for you to offer an enhanced level of customer service.
Whether you’re an agency, a contractor, or manage marketing in-house for an organization, here are some security measures our own Technical Director Matt Gallant inspired us to lean into that you may want to think about and incorporate into your work.
THE CHALLENGE: Remote Work
We’re not control freaks, but remote work introduces security complexities and compliance issues companies haven’t dealt with before.

This includes people using old / outdated / unprotected computers and connecting to the internet through personal routers that you can’t monitor or regulate.
The connection of these endpoint devices (i.e. laptops, tablets, mobile phones, internet-of-things devices, and other wireless implements) to your network creates attack paths for security threats to your clients’ or your own networks and information.
THE SOLUTION: A VPN
Install a company Virtual Private Network (VPN) so you’re all on the same IP address.
A secure tunnel for online browsing, a VPN allows remote team members to browse through a secure and encrypted internet connection.
This ensures secure communication, minimizes data theft incidents, and actually improves privacy. All this without making employees feel mistrusted or big brother-ed.
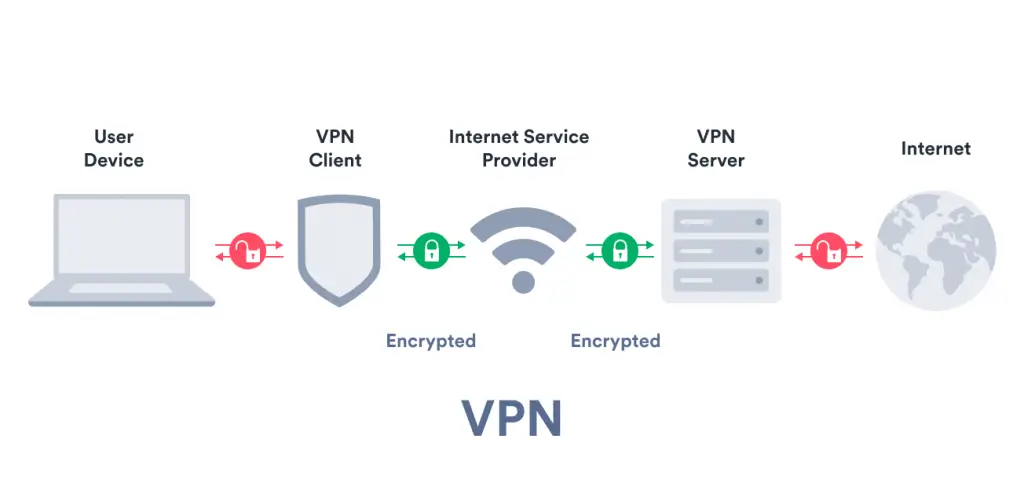
Source: SURFSHARK
And (depending on your choice of VPN), it’s usually seamless for your team and affordable for your organization.
Most VPN solutions for businesses are less than $10/month/user. We’re big fans of ExpressVPN, but here are several other solid options.
THE CHALLENGE: Balancing Access with Risk
Social media is a key channel for cybercriminals.
From ransomware that holds data hostage until victims pay a ransom to hacked accounts that generate incriminating posts and ruin your brand and reputation, these are risks you don’t want to expose your clients to or take on yourself.
THE SOLUTION
1) Limit the number of users who have access to your social media accounts and those you manage for clients. The more hands that touch accounts, the more risk you invite. It’s essential to limit user access so you can easily narrow and control entry points.
2) Implement two-factor authentication (2FA) for said users. It’s now mandatory for Facebook accounts, Twitter is headed this direction (for Apple devices at the moment), and LinkedIn requires all Recruiter and Talent Hub users to turn it on in order to access their accounts. We suspect it’s a matter of time before all platforms require it.

3) Practice password zen (it’s a thing). We get the temptation to go with the easy and memorable, but a complex password dramatically reduces your risk of getting hacked. Set a policy and train your team. Here’s a list of last year’s top passwords you’ll want to avoid.
4) Implement an enterprise password manager. Here’s a list of excellent password manager choices. Some offer advanced protection like dark web monitoring and remote account deletion. At minimum, we recommend you choose one that has 2FA, password vaults, and secure password sharing (with your team and clients).
THE CHALLENGE: Website Security
As a marketer, it’s rare for the site(s) you manage to be one(s) you built, so it’s possible vulnerabilities exist you might not know about. Here are some blind spots we commonly see and invest in solving.
THE SOLUTION
1) Make cybersecurity inherent in site builds. That way you don’t have to tack it on later. It pays to empower website managers by teaching them how to navigate and keep security in mind as they make updates themselves.
2) Build site themes from scratch. Templates offer easy back-door access for bad actors.
3) Block files that provide external access (like ones that allow comments). It’s a small investment that offers big bang-for-buck on your overall security posture.
4) Avoid WordPress plug-ins whenever possible. Yes, they’re tempting quick fix solutions. But they plant code written by who-knows-who that can do who-knows-what to your site. Plus, they’re not always maintained, so the more you add, the more risk you assume. If you find one you can’t live without, make sure it has high ratings before you install it. Use auto-pilot programs, which allow you to update plug-ins automatically and more safely.
5) Install Sucuri Security. It’s a free WordPress plug-in that comes with hardening features, malware scanning, core integrity check, post-hack features, and email alerts. Yes, we realize how ironic that is with tip #4 in mind, but it’s a highly rated plug-in, updated constantly, and is built to keep the threats out.
THE CHALLENGE: Privacy
With last year’s iOS 14.5 application tracker transparency, Google and Amazon making the list of the top 5 companies fined most heavily for GDPR violations, the forthcoming end of 3rd party cookies as we know them, and Google Tag manager vulnerabilities we’ve discovered – the privacy landscape makes balancing digital advertising with data protection more complex than ever.
THE SOLUTION: Heightened Data Sensitivity
Be intentional about privacy and prioritizing protection of both customer and internal data. Here’s what that looks like:
1) Create and routinely train staff on policies around the handling, storage, and transmission of data. Make it part of your onboarding process.
2) Institute password policies and managers so all your internal and client passwords reside in a central, secure place and receive regular updates. Use the sharing feature so clients and staff always have secure access.

3) Implement real-time monitoring so you can watch over and manage all your organizational data access.
4) Review your audit logs. This will give you direct insight into all IT – including suspicious – activity.
Ogres Have Layers. So Does Effective Cybersecurity.
There are many pieces to creating a tight security posture, and know that you’ll never achieve nirvana. Security is about layers of protection.
The more you can put between you and criminals, the more you slow them down, and the more likely attacks are to fail.
Try to stay on top of emerging threats and best practices so you model positive security and provide sage advice to your organization and your clients.
Here are some great news sources to help you stay on top of issues and solutions – just like the information security pros out there.
Marketing and cybersecurity are changing fast. Find a partner dedicated to staying on top of them both.